
LogRhythm's Security Intelligence Platform
Efficiently Build a Modern Security Operation
Selecting a platform upon which to build your security operation is one of the most important strategic decisions you’ll make. It has to meet your immediate needs and it has to scale over time. It shouldn’t require costly integrations or customizations to realize your goals. Modernize your security operations with the powerful and integrated capabilities of our Security Intelligence Platform.
Overview:
End-to-End Threat Management in One Platform
You need deep, real-time visibility into your entire IT environment to defend your organization from today’s threats. LogRhythm analyzes all of your forensic data. It fills gaps with endpoint and network sensors. With LogRhythm, you get the intelligence and tools you need to protect your network.

Flexible Data Collection
Assemble all of your machine data. Gather all the forensic evidence generated by your IT environment with our collector tier—with or without agents.
Forensic Data Generation
Fill in your forensic data gaps with endpoint and network monitoring. Our network and endpoint sensors ensure that you have all of the forensic detail you need to detect advanced threats.
Machine Data Intelligence Fabric
Get the intelligence you need—without the noise. We process, structure and contextualize your data for over 750 different sources. You get faster, more accurate analytics with machine data intelligence fabric. Learn more about LogRhythm Labs & Machine Data Intelligence Fabric.
Machine Analytics
Get real-time protection from threats. Automate multi-dimensional machine analytics, including sophisticated techniques such as machine learning, behavioral profiling, statistical analysis, blacklisting, whitelisting and correlation. Learn more about Security Analytics.
Forensic Analytics
Search through terabytes of data. Find the forensic evidence you need faster. Get the information you need when you need it with structured and unstructured search—in a single, easy-to-use interface.
Actionable Intelligence
You need the right information at your fingertips to respond to threats fast. We deliver the information you need in the most useful way so you can respond to the most critical threats quickly.
Incident Response Orchestration
Streamline incident response. Neutralize threats faster. Our fully integrated automation, collaboration and workflow tools enable you to prioritize and neutralize threats immediately and efficiently.
Advanced Intelligence (AI) Engine
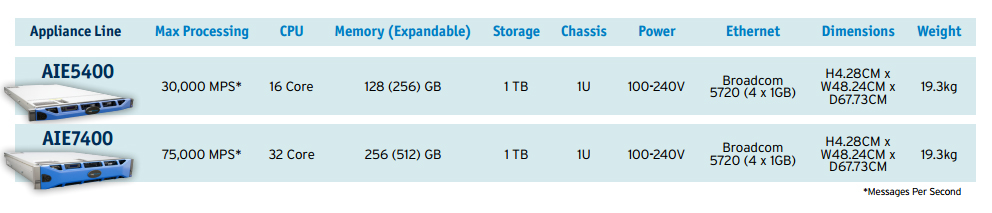
AI Engine Delivers Real-Time Visibility to Risks, Threats and Critical Operations Issues
LogRhythm’s AI Engine is a fully integrated component of the LogRhythm platform, delivering automated, continuous analysis and correlation of all activity observed within the environment. With a uniquely flexible and comprehensive approach, it delivers realtime visibility to risks, threats and critical operations issues that are otherwise undetectable in a practical way. AI Engine is correlation that works.
With over 900 preconfigured, out-of-the-box correlation rule sets and a wizard-based drag-and-drop GUI for creating and customizing even complex rules, AI Engine enables organizations to predict, detect and swiftly respond to:
- Sophisticated intrusions
- Insider threats
- Fraud
- Behavioral anomalies with users, networks and endpoints
- Compliance violations
- Disruptions to IT services
- And many other critical actionable events
Comprehensive Advanced Correlation
Unlike legacy SIEM solutions, AI Engine leverages its integration with the log and platform management functions within the LogRhythm platform to correlate against all data—not just a pre-filtered subset of security events. Seamless integration also enables immediate access to all forensic data directly related to an event.
AI Engine rules draw from over 70 different metadata fields that provide highly relevant data for analysis and correlation. This metadata includes the dynamic Risk Based Prioritization (RBP) value assigned to all machine data, enabling the AI Engine to build trends and expose statistical anomalies based on the risk level associated with specific activity on the network. Whether detected by out-of-the-box rules or user-created/modified rules, AI Engine identifies and alerts on actionable events with tremendous precision, supporting security, compliance and operations use cases. AI Engine can also be used to cast a wide net through generalized correlation rules for broader visibility that accommodates changes in event behavior.
Multi-Dimensional Analytics
LogRhythm has combined enterprise-wide advanced correlation and pattern recognition with automated behavioral and statistical analysis to deliver the industry’s first Multi-dimensional Analytics capabilities. By combining advanced statistical and heuristic analysis with behavioral whitelisting, LogRhythm enables organizations to automate the process of learning what constitutes “normal” behavior on any combination of attributes tied to users, hosts, applications, or devices. Integrating these capabilities with advanced correlation and pattern recognition eliminates three significant problems for users of 1st generation SIEMs: the inability to accurately define what constitutes “normal” activity, a deluge of false positives that reduce understanding of meaningful events, and uncertainty due to false negatives.
AI Engine Delivers Users With:
- Advanced correlation against all log and machine data
- Generalized and targeted threat management and compliance automation suites
- Automated behavioral and statistical baselines
- Immediate access to underlying forensic data
- Extensive out-of-the-box advanced analytical rules
- Unparalleled ease of use
AI Engine in Action
AI Engine’s numerous predefined advanced correlation rule sets are configured to run out-of-the-box and act as templates for easy customization. All rules within AI Engine can be quickly modified through a highly intuitive GUI to address the unique requirements of any organization.
Secure
A single event is not always enough to indicate a breach or show the true reach of a security incident. AI Engine automatically generates behavioral whitelists of “normal” activity to help identify suspicious behavior patterns and automatically identify and alert on potential threats and breaches. For example, malware can invade and spread through an organization quickly, exposing data and weakening security faster than administrators can react. In many cases, the extent of the damage is unknown.
Examples:
- Malware is detected on a host, followed by multiple outbound attacks from that infected host
- Suspicious communication from an external IP Address is followed by data being transferred to the same IP Address
- A user logs in from one location, and then logs in from another city or country soon afterward
- RBP score assigned to firewall logs steadily increases from 50 to 90 over the course of an hour
Comply
AI Engine enforces continuous compliance by generating events when specific policy violations occur. These include protecting cardholder data or Protected Health Information (PHI) from unauthorized access and actively monitoring privileged user behavior.
Examples:
- Five failed authentication attempts followed by a successful login to a database containing ePHI, followed by a large data transfer to the user’s machine, all within 30 minutes
- A file containing credit card data is accessed, followed by an attempt to transfer information from the same host to a USB thumb drive within 10 minutes.
- Multiple new accounts are created, granted escalated privileges, and then access critical data in a short period of time
Optimize
Advanced correlation offers substantial value for operational insight and IT services assurance. Slight variations in specific activities or a particular sequence of typically common operations events may indicate critical operations issues.
Examples:
- A backup process is started, but no log is generated, indicating that the backup completed
- A critical process stops and doesn’t start back up within a specific timeframe
- A large group of servers shuts down, followed by a smaller group of servers starting back up
- High I/O rates on a critical server, usually only observed after-hours during backup procedures, are observed during normal business hours
AI Engine Deployment Options
As a fully integrated component of any LogRhythm deployment, AI Engine can be deployed as a dedicated, high-performance appliance, installed as software on dedicated customer equipment, or deployed on multiple virtualization platforms, including VMware ESX, Microsoft Hyper-V, and Citrix XenServer. High-performance appliances can process tens of thousands of logs per second and billions of logs per day. AI Engine possesses a horizontally scalable architecture, allowing for simplified, incremental expansion of the deployment to meet the processing volume requirements of any enterprise. All instances of AI Engine are centrally managed through the LogRhythm client console.
High-Performance Component-Based Architecture:
Whether you’re a medium-sized company or a Fortune 500 enterprise, we meet your scalability and performance requirements. Our flexible component architecture realizes a wide variety of solutions with a building block approach. Add functionality and capacity as your needs evolve to efficiently scale your LogRhythm deployment based on your unique requirements.
Data Collector
Data Collector provides local agent-based or remote agentless collection of machine data, including log messages, security events and flow data. Learn more about Endpoint Monitoring and Forensics.
System Monitor
System Monitor is an agent-based sensor that independently monitors host-level activity. Monitored activities include user authentications, file modifications, active applications and network communications. System Monitor generates real-time forensic data to support your analytics-driven threat detection and incident response.
Network Monitor
Network Monitor performs deep packet inspection of network traffic for application identification, extraction of searchable application-level metadata and full packet capture.
Its internal analytics engine provides run-time Deep Packet Analytics™. Network Monitor forwards full session SmartFlow™ records for analytics-driven threat detection and incident response. Learn more about Network Monitoring and Forensics.
Data Processor
Data Processor provides patented, high-performance, distributed and highly available processing of machine and forensic data received from data collectors, system monitors and network monitors. Data Processor transforms this data into a contextualized form to create the Machine Data Intelligence Fabric that underlies our analytics and platform capabilities.
Data Processor archives and distributes both original unstructured data and structured metadata to other platform components to support indexing, automated machine analytics and alarming. Learn more about High-Performance Appliances.
Data Indexer
Data Indexer provides high-performance, distributed and highly scalable indexing of machine and forensic data received from data processors. It stores data in support of centralized search and forensic analytics. You can deploy multiple data indexers in a high availability cluster to serve massive workloads and a high number of concurrent users.
AI Engine
AI Engine’s patented stream-based machine analytics technology provides real-time, automated analysis of contextualized machine and forensic data received from data processors. It supports a variety of automated analytic techniques, including machine learning, behavioral profiling, statistical analysis, whitelisting, and blacklisting. You can deploy multiple AI Engine nodes to support distributed analysis and workload scaling.
Platform Manager
Platform Manager performs alarming, notifications, incident response orchestration, workflow automation and centralized administration for our platform. Platform Manager provides Web and application services, enabling centralized structured and unstructured search, forensic analytics, reporting and real-time dashboards. Platform Manager also delivers our open platform API to support third-party integrations.
Analytics Modules
Analytics modules are created and maintained by LogRhythm Labs to help our customers achieve rapid time-to-value. Modules include pre-packaged content like machine analytics rules, searches, reports and dashboards.
Improve your security posture with threat management modules such as User Threat Detection and Endpoint Threat Detection. Adhere to complex regulation systems with LogRhythm’s compliance automation modules, which support PCI, SOX, HIPAA, and more.
Elasticsearch & Patented Processing:
Elasticsearch is fast becoming the technology of choice for storing structured and unstructured machine data in support of search-based analytics. LogRhythm combines our patented data processing technology with Elasticsearch-based indexing to deliver the most capable and scalable machine data analytics platform in the market. On top of that, you can deploy LogRhythm data processors and data indexers in a matter of minutes.
Do you require the highest levels of performance and availability? Then deploy an active/active architecture and benefit from its inherent cost efficiencies and performance benefits.
Documentation:
Download the Collector Technology (PDF).
Download the Precision Search (PDF).
Download the Security Intelligence Model Whitepaper (PDF).
Download the Processing & Indexing Architecture (PDF).
Download the AI Engines (PDF).
Pricing Notes:
- Pricing and product availability subject to change without notice.
