
LogRhythm Solutions - Security
Detect, respond to and neutralize cyber threats before they cause damage to your business.
LogRhythm Threat Management Ecosystem
Threats Have Evolved—Has Your Security Program?
The perimeter is gone. Data is everywhere. Threats are sophisticated and motivated. It’s never been more important for you to detect and respond to them quickly. They use many direct and indirect attack vectors. The volume of security alarms is overwhelming. Prevent threats, attacks and compromises to your IT infrastructure from damaging your business by proactively managing the attack lifecycle.

Detect and Kill Threats Early
Data breaches don’t happen overnight. Threats must first penetrate your environment and then be allowed to operate undetected—for weeks or even months. To avoid data breaches and other damaging cyber incidents, detect and kill threats early in their lifecycle.

Reconnaissance
The threat actor assesses your defenses, and how to perform the initial compromise. Whether through spear phishing, remote zero-day exploit, physical compromise or stealing credentials, they will find a way in.
Initial Compromise
The threat actor determines their target and gains initial entry to your network. This could be a compromised endpoint device or a compromised account. They can now authenticate within the internal network.
Command & Control
The threat actors put back doors and remote access tools (RATs) in place. They can now stealthily return at any time to continue their mission.
Lateral Movement
The threat actor scans your internal network, identifying additional targets. They compromise more systems and more user accounts. Their foothold and access in your environment is now widespread.
Target Attainment
The threat actor identifies and finally gains access to the systems of interest. They now have all the access they need to realize their objective.
Exfiltration, Corruption and Disruption
The threat actor realizes their mission. They might siphon off data via covert communication channels. Or they might disrupt a critical business operation. In either case, they have done real damage. The costs for your organization to recover could now measure in the millions.
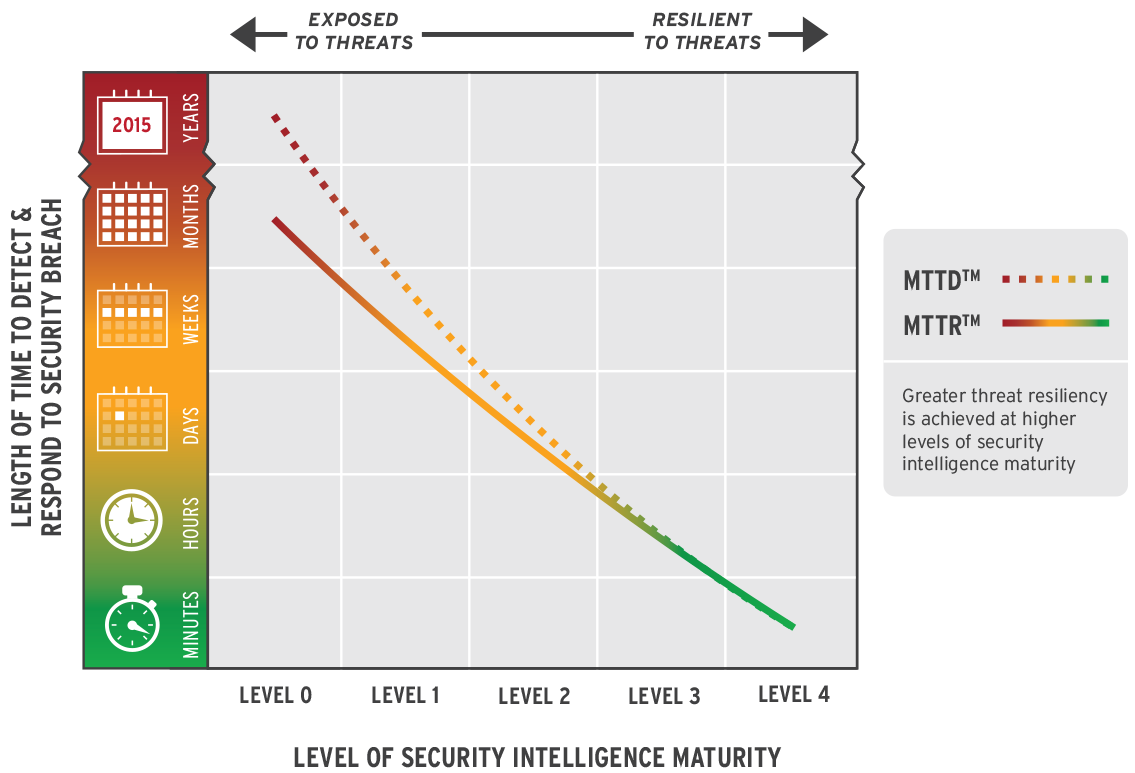
Dramatically Reduce Detection and Response Times
To kill threats quickly, you need to accelerate time to detection and time to response. This requires efficiency of operations and a well-enabled team. The LogRhythm platform optimally serves both needs by delivering end-to-end Threat Lifecycle Management. Efficiently reduce your mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) with LogRhythm.
Streamline Your Security Operations
The effectiveness of your security monitoring and response program is largely determined by the efficiency of your workflows. How many alarms can your team qualify every day? How many investigations can they conduct? How quickly can they respond to incidents?
Your answers to these questions are either enabled or impeded by workflow efficiency. The LogRhythm Security Intelligence Platform delivers a streamlined workflow, from detection through mitigation to full recovery. You’ll see more, investigate more and respond more quickly.
Collect
You can’t detect what you can’t see. LogRhythm collects machine data from across the enterprise and augments this machine data with critical context. LogRhythm’s network and endpoint forensic sensors provide further visibility across the extended IT environment. Learn more about Log Management.
Discover
Our big data analytics approach ensures no threat goes unnoticed. Machine analytics automatically analyze all collected data, detecting both routine and advanced threats automatically. Our powerful search capabilities enable your team to efficiently hunt for threats. Learn more about Security Analytics.
Qualify
The LogRhythm Security Intelligence Platform automatically qualifies all threats with a 100-point risk-based priority score so your team knows where to spend their time. Alarms can be quickly qualified with immediate access to rich forensic detail displayed in user-friendly analysis tools.
Investigate
Ensure that threats don’t slip through the cracks. Enable collaborative investigations by using our embedded incident response capabilities. Obtain real-time visibility into active investigations and incidents with dashboards and live activity feeds.
Mitigate
Our SmartResponse™ automation framework helps you configure pre-staged actions to automate common investigatory steps and mitigations. Enable your analysts and incident response team to investigate and kill threats more quickly.
Recover
Collateral damage often exists after an incident. If you detect the threat late in the lifecycle, you run the risk of additional systems and accounts being compromised. LogRhythm’s incident response orchestration provides central access to all required information. Collaborative workflows bring teams together for rapid recovery.
Workflows that Work
Don’t piece together your workflows–implement a unified workflow for end-to-end threat detection and response. Enable early eradication and avoid the breach.
Use LogRhythm’s built-in incident response orchestration platform to streamline your security operation, accelerate your threat response and reduce risk for your organization. You’ll be able to detect more threats and respond to more incidents.
LogRhythm User Behavior Analytics & Insider Threat Detection
Stop Insider Threats and Detect Stolen Accounts
You can only shut down compromised accounts if you can see them. Illuminate insider threats and stolen credentials with User Behavior Analytics. Catch imposters, identify privilege abuse and stop user-based threats.

Quickly Spot Dangerous User Activity
Don’t let threatening users fly under your radar. Arm yourself with User Behavior Analytics (UBA), which gives you extensive visibility into insider threats, compromised accounts, and privilege abuse. LogRhythm Labs regularly releases new UBA content, including behavioral profiling and peer group analytics, statistical analytics, and advanced correlation.
Identify Insider Threats
Malicious insiders cause damaging, headline-making cyber breaches and acts of sabotage. Monitor for data exfiltration, sabotage, policy violations, and other dangerous activity.
Uncover Compromised Accounts
Breaches usually involve multiple user accounts. Distinguish between legitimate accounts and compromised accounts by identifying anomalous activity. Expose the imposter before a breach occurs.
Expose Privilege Abuse
Your IT team has the keys to kingdom. Malicious parties can often infiltrate organizations by bribing or extorting an insider. Spot privilege abuse and account compromise before damage occurs.
Spot Brute-Force Attacks
Attackers will programmatically target your cloud-based infrastructure and external authentication systems. Know when you’re a target so you can block access.
Identify New Privileged Accounts
It can be challenging to ensure appropriate access rights and keep track of superusers. LogRhythm helps you automatically monitor and report on the creation of privileged accounts and the elevation of permissions.
Track Data Access & Exfiltration
When a compromised user account or a rogue insider finds their way to sensitive data, you need to know. Our analytics can help you detect when a user inappropriately accesses protected data.
Streamline Your Security Operations
Achieve full situational awareness on a unified Security Intelligence Platform that delivers UBA, SIEM, and more. Corroborate user anomalies with other network and endpoint events to identify previously undetected threats and drive down false-positives. Automate and orchestrate incident investigation and response from a single pane of glass.
Identify the Actors Behind the Actions
Knowing who is behind every action is critically important when investigating threats and incidents. Unfortunately, many log messages don’t contain this information.
Fill in the gaps with Identity Inference, which determines who is behind an action by observing the data we already capture, strengthening your User Behavior Analytics.
LogRhythm Network Threat Detection and Behavior Analysis
Detect Network Anomalies, Shut Down Network Threats
You can only stop attackers from gaining an initial foothold in your network or using it to expand their presence if you can see them. Illuminate compromised systems and insider threats with LogRhythm’s machine learning and behavioral analytics. Expose advanced malware, detect zero day attacks, identify compromised systems and stop the threat.

Stay a Step Ahead
Make sure no network threat remains hidden with our Network Threat Detection Module (NTDM). LogRhythm Labs built this module to give you the thorough visibility you need to identify threats quickly. The Labs team provides ongoing updates to help you stay a step ahead.
Expose Advanced Malware
Advanced malware can easily evade traditional endpoint protection solutions. When the malware goes active, behaviors on the infected host will change. Our behavioral analytics will detect this and raise the alarm.
Detect Zero-Day Attacks
If an attacker comes at you with a zero-day, intrusions will occur. When the attacker uses compromised systems to further their foothold, LogRhythm detects behavioral changes so you know what’s happening right away.
Quickly See Malware Outbreaks
Left undetected, malware can quickly propagate across your network. LogRhythm integrates with a variety of endpoint protection platforms. You’ll know what’s happening at the first sign of an outbreak.
See Internal Port Probes
Once inside, an attacker will scan and probe the internal environment to find new targets. We’ll detect these scans, even when they are “low and slow.”
Detect Denial of Service Attacks
Disruption of services is another motive for cyberattacks. LogRhythm detects significant behavioral deviations and patterns known to indicate that a DoS attack is occurring—both internally and externally.
Expose Covert Network Channels and Data Exfiltration
To prevent a breach, you have to be sure that attackers are not accessing your network covertly or using it to exfiltrate data. LogRhythm’s advanced analytics will detect covert communication channels so you can rest easy knowing that your network is protected.
Clear Visibility into Network Communications
Your data quality dictates the sophistication of your analytics-driven intelligence. When you combine our Network Monitor sensors with our Network Threat Detection Module, you get the most comprehensive network behavioral analytics solution available. The deep visibility into network communications provided via SmartFlow™ is leveraged by AI Engine to model unique behaviors and more accurately detect threats. With full packet capture, your incident response team has full fidelity insight into network sessions.
Know What’s Normal—and What’s Not
Sometimes a single behavioral shift isn’t enough to warrant investigation. But multiple behavioral changes should raise the alarm.
Detect shifts across multiple network behaviors. Correlate behavioral changes against other threat indicators. LogRhythm’s multidimensional behavioral analytics give you higher-quality, corroborated intelligence. If your IPS warns of a possible attack and LogRhythm observes a behavioral shift on the targeted server, you’ll know.
Endpoint Threat Detection
Defend the Endpoint, Protect the Center
In just one click, a threat actor could compromise an endpoint through a spear phishing attack. Your internal servers are vulnerable to threats operating from within.
Traditional endpoint protection is no longer up to task. You need a second line of defense. Combining real-time endpoint monitoring with big-data analytics can detect advanced attacks and insider threats. This visibility also provides incident responders access to rich forensic data that can expedite investigations. Get the visibility you need with System Monitor.
Features
Enterprise-Grade Visibility
Protect your enterprise from the unknown. Detect advanced attacks on endpoints and servers. Enable fastest incident response. System Monitor gives you deep visibility into the threats faced by your endpoints. It has a lightweight footprint, support for multiple platforms and policy-based administration. Get the clarity you need for peace of mind for a low cost of ownership.
Real-Time Continuous Activity Monitoring
You can think of System Monitor as a DVR. It continuously records activity occurring on the monitored host in real-time. This data is transmitted and safeguarded for analytics and incident response support.
File & Registry Integrity Monitoring
Unexpected changes to files or the windows registry can indicate the presence of a threat. Detect them and identify change management processes gone awry. Learn more about File Integrity Monitoring.
Process, Network and User Monitoring
System Monitor records local process activity, network communication and user activities. This data is used to detect the presence of advanced malware and other threats.
Removable Media Monitoring
Rest assured knowing that you’re recording when all data transferred to a USB drive and other writeable media. If data leaves your building by foot, you’ll know. With System Monitor, you can also prevent data loss by disabling writable media.
Multi-Platform and POS Support
Our platform works with a wide variety of Windows, Linux and Unix operating systems. We also support point-of-sale systems to help customers detect retail cybercrime. Learn more about Cyber Crime and Fraud.
Administration
Keep administrative costs low with policy-based configuration and centralized administration. Agent upgrades occur in seconds with the click of a button.
Large Enterprise Scalability
We built our platform for scale. With our enterprise-grade administration, you can deploy and manage tens or hundreds of thousands of agents cost effectively.Turn Up the Volume
The volume of data generated by endpoint monitoring solutions can be significant. Easily deploy System Monitors to sit silently on hosts. When you need to see more, centrally turn up the volume in seconds.
LogRhythm Cyber Crime Detection
Over the past few years, several retail organizations have been hit with high-profile data breaches that have left millions of customers’ credit card details and personal information exposed.
Retailers will continue to be prime targets for motivated cyber criminals targeting sensitive and lucrative customer data, and must take steps to secure delicate information.
LogRhythm’s Retail Cyber Crime Security Analytics Suite was specifically designed to help retail organizations properly configure and monitor their IT environment to achieve a complete forensic view into anomalous and malicious activity.
This includes everything from activity on point-of-sale (POS) system endpoints to the payment processor, as well as back-office and network infrastructure. The Retail Cyber Crime Suite provides the continuous monitoring needed to detect behavioral changes and attacks within the cardholder data environment, expediting remediation and breach containment, and minimizing data loss and brand exposure.
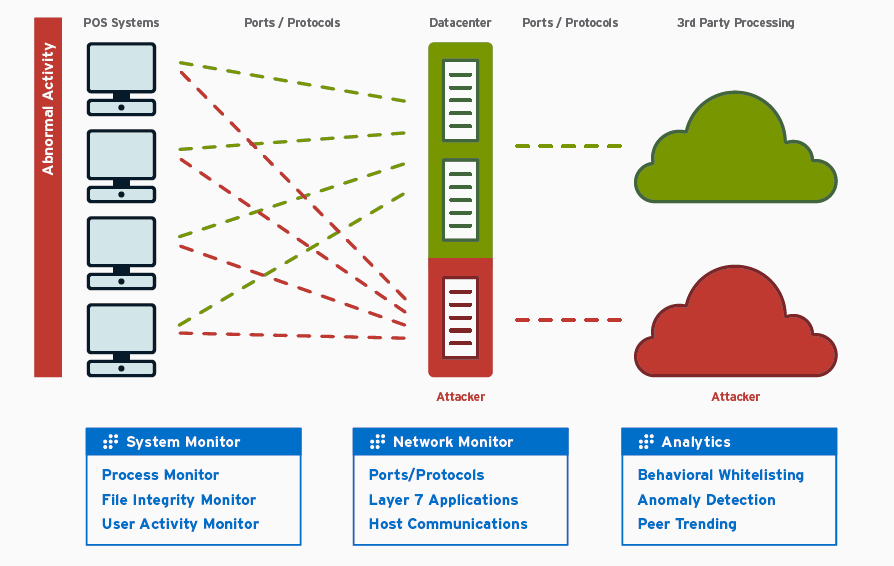
Benefits of LogRhythm’s Retail Cyber Crime Security Analytics Suite include:
- Correlate all data from highly distributed retail environments for a complete view into payment processing chain
- Establish a “gold standard” to detect anomalous and malicious activity on POS systems
- Quickly identify early indicators of cyber-attacks on the payment processing chain to effectively detect and contain breaches
Threat Intelligence
Threats are dynamic and attack vectors change constantly. Respond quickly and minimize damage by using the rich external context enabled by threat intelligence. Immediately know about dangerous IP addresses, files, processes, and other risks in your environment.
LogRhythm seamlessly incorporates threat intelligence from STIX/TAXII-compliant providers, commercial and open source feeds, and internal honeypots, all via an integrated threat intelligence ecosystem. The platform uses this data to reduce false-positives, detect hidden threats, and prioritize your most concerning alarms.
Threat Intelligence Standards
STIX/TAXII
STIX (Structured Threat Information eXpression) is a language for describing cyber threat information in a standardized and structured manner. The Trusted Automated Exchange of Indicator Information (TAXII) provides a trusted, automated exchange of cyber threat information captured in STIX format. These are part of an open, community-driven effort and offer free specifications to help automate the exchange of cyber threat information. LogRhythm provides the ability to add custom STIX/TAXII compliant providers, such as Soltra Edge, enabling organizations that participate in industry-specific or government-led trusted exchanges to easily incorporate threat intelligence into LogRhythm.
Commercial Threat Intelligence Feeds
Anomali
Anomali makes it possible to correlate tens of millions of threat indicators against your real time network activity logs and up to a year or more of forensic log data. Anomali’s approach enables detection at every point along the kill chain, making it possible to mitigate threats before material damage to your organization has occurred.
Cisco
Cisco AMP Threat Grid combines static and dynamic malware analysis with threat intelligence into one unified solution. You get timely, in-depth information you need to protect your business from malware of all types. It integrates real-time behavioral analysis and up-to-the-minute threat intelligence feeds with existing security technologies, protecting you from both known and unknown attacks.
CrowdStrike
CrowdStrike stops breaches by preventing and responding to all types of attacks—both malware and malware-free. CrowdStrike has revolutionized endpoint protection by combining three crucial elements: next-generation AV, endpoint detection and response (EDR), and a 24/7 managed hunting service, all powered by intelligence and uniquely delivered via the cloud in an integrated solution.
Recorded Future
Recorded Future arms you with real-time threat intelligence so you can proactively defend your organization against cyber attacks. Its patented Web Intelligence Engine continuously analyzes the entire Web, giving you unmatched insight into emerging threats. Recorded Future helps protect four of the top five companies in the world.
Symantec
Symantec DeepSight Intelligence provides actionable data about malicious activity sources, emerging threats, and vulnerabilities. DeepSight Intelligence data feeds are derived from proprietary analysis of billions of events from the Symantec Global Intelligence Network. This intelligence can reduce exposure to threats, allowing businesses to act appropriately and quickly, preventing security incidents before they happen.
Webroot
Webroot® is the market leader in cloud delivered security software as a service (SaaS) solutions for consumers, businesses and enterprises. Webroot delivers real-time advanced internet threat protection to customers through its BrightCloud security intelligence platform, and its SecureAnywhere suite of security products for endpoints, mobile devices and corporate networks.
Open Source Threat Intelligence
Want to leverage open source threat feeds? LogRhythm helps you rapidly incorporate threat intelligence from several open source providers:
- Abuse.ch
- AlienVault
- AutoShun
- HailaTaxii Open Source Feed
- Malware Domains
- PhishTank
- SANS-ISC
- SpamHaus
- TOR Network
Honeypot & Deceptive Analytics
Cyber attacks are becoming increasingly targeted in nature, making it imperative for organizations to deploy security tools that enable the detection and prevention of targeted attacks. When deployed and analyzed correctly, honeypots provide organizations an increased awareness of attack and breach activity generating dynamic threat research unique to the customer environment they are targeting.
LogRhythm’s Honeypot Analytics allow customers to centrally manage and continuously monitor honeypot event activity for adaptive threat defense. When an attacker begins to interact with the honeypot, LogRhythm’s Security Intelligence Platform begins tracking the attacker’s actions, analyzing the honeypot data to create profiles of behavioral patterns and attack methodologies based on the emerging threats.
Our AI Engine performs real-time, advanced analytics on all activity captured in the honeypot, including successful logins to the system, observed successful attacks and attempted/successful malware activity on the host. This automated and integrated approach to honeypots eliminates the need for the manual review and maintenance associated with traditional honeypot deployments.
The Honeypot Security Analytics Suite delivers:
- Continuous monitoring of honeypot data
- Customized threat research for strategic defense
- Automated breach prevention and response
- Dynamic security intelligence
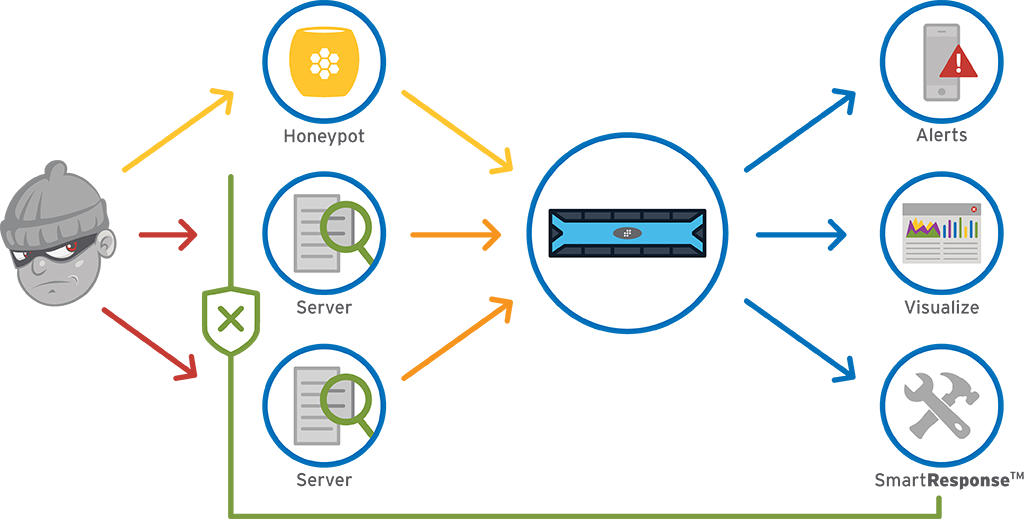
LogRhythm’s Honeypot Security Analytics Suite generates threat intelligence specific to the targeted environment, allowing organizations to identify their adversaries, recognize their attack patterns and take the necessary steps to prevent attacks from infiltrating the corporate network. Research from the LogRhythm Labs team is continually embedded in the suite.
Use Scenarios
Compromised Credentials
Challenge: The majority of attacks exploit valid user credentials to gain unrestricted access to the corporate network. Organizations need an effective means of monitoring for insecure accounts and passwords to prevent credentials from being compromised.
Solution: LogRhythm’s Honeypot Security Analytics Suite provides AI Engine rules that monitor for successful and unsuccessful logon attempts to honeypot servers, capturing details on the username and password. This allows analysts to see commonly attempted username and password combinations on the honeypot hosts.
Benefit: By knowing which accounts are being targeted by hackers and which passwords are vulnerable to exploit in the honeypot, organizations are able to strategically increase defense measures within their network by monitoring at risk user accounts and enforcing stricter password policies. A SmartResponse™ plugin can automatically add the IP address observed in the honeypot to a firewall list to prevent interaction with the corporate network.
Zero-Day Malware:
Challenge: With the evolving sophistication and rapid propagation of new cyber attack campaigns, it is difficult for organizations to detect zero-day exploits using traditional security tools because they lack the signatures and behavioral profiles needed to spot targeted malware.
Solution: LogRhythm’s Honeypot Security Analytics Suites attracts attackers to a honeypot server configured for optimal surveillance. When a honeypot host is successfully compromised, LogRhythm captures the full details about how attackers gained access along with the subsequent host interactions.
Additionally, LogRhythm AI Engine rules capture and parse out all attempted malware and exploit downloads including communication with command and control servers.
Benefit: This data allows the security team to perform detailed threat analysis, giving them new insight into upcoming malware payloads and attack methodologies employed by adversaries. LogRhythm also captures additional environment data, such as user-agent strings, which highlight the tools that attackers or bots are using to breach networks. SmartResponse™ plugin can automatically add the attackers to an internal threat list to block access to the corporate network.
LogRhythm File Integrity Monitoring
Strengthen Security, Streamline Compliance
Protect your organization’s critical files, wherever they’re stored. Alert on malware-related registry changes, improper access of confidential files, and theft of sensitive data
User-Aware File Integrity Monitoring
Continuously monitor all files. Easily see who has changed what.
View User & File Activity Holistically
Pivot from a file access or change to a specific user. View a full timeline of their activity, including both FIM and other behavior information.
Monitor What Matters
Selectively monitor file views, modifications and deletions, and modifications, as well as group, owner and permissions changes.
Enrich Your Security Analytics
Use data generated by FIM to solve new use cases for User Behavior Analytics (UBA) and Endpoint Threat Detection.
Alarm on Unauthorized Changes
Alarm on an unauthorized change to sensitive files and registry settings, whether caused by an attack or a change management error.
Identify Abnormal Behavior
Alert on anomalous user activity related to important files. Reduce false positives by corroborating with other data.
Achieve Rapid Time-to-Value
Configure FIM to protect your files and intellectual property using out-of-the-box policies for many common applications.
Comply and Secure
Address over 80 PCI DSS control requirements and many core HIPAA requirements. Alert and report using out-of-the-box FIM policies. Streamline your compliance objectives so you can focus on your most important security priorities.

Reduce Total Cost of Ownership
Efficiently deploy and manage your agents with centralized, policy-based configuration and administration. Simplify administration by applying layered policies to each agent, rather than creating a new policy for each new situation. Accelerate time-to-value by protecting your most important files with preconfigured policies for a variety of operating systems and applications.
Deploy on Windows, Linux and UNIX systems.
Achieve More on a Unified Platform
Get FIM as an embedded part of LogRhythm’s Endpoint Monitoring & Forensics solution, a lightweight agent that also provides activity monitoring and process monitoring.
Endpoint Monitoring & Forensics is an integrated component of our Security Intelligence Platform, helping you gain pervasive visibility and reduce your total cost of ownership.
FIM in Action
Problem: You need to know if an attacker installs malware on your point-of-sale systems in an attempt to begin exfiltrating cardholder data.
Solution: Detect POS infiltration as soon as it begins by alerting on malware-related registry changes.
Problem: You spend significant time collecting data and creating reports for compliance audits (e.g., PCI DSS and HIPAA).
Solution: Generate reports on file access and other user activity rapidly. Give compliance auditors the data the need in the format they require.
Problem: You need to mitigate user-based threats to privileged files (e.g., payroll files) from both insiders and outsiders.
Solution: Enrich your User Behavior Analytics with FIM data to identify users with anomalous file access behavior. See all that a user does before and after unusual access behavior.
Problem: A server has been improperly accessed and you need to know if sensitive files have been leaked.
Solution: Secure a complete set of forensic data to rapidly identify the cause and scope of the security incident.
LogRhythm's Security Operations Center Platform
Arm Your Team to Protect Your Organization
Security leaders understand that accelerating threat detection and response requires a Security Operations Center (SOC). But building a SOC that works well for your organization requires strong people, processes, and technology that you may not have in place yet. Whether you’re building a one-person virtual SOC or a 24x7 global operation, LogRhythm’s Security Intelligence Platform and SOC Enablement Services can help you achieve success. Work with us to:
- Build an intelligence-driven SOC to efficiently monitor attacks and respond to threats
- Align your SOC platform with your organization through enablement services
- See a greater ROI on your SOC investment with LogRhythm’s unified solution
Build an Intelligence-Driven SOC
Your SOC should be built on an integrated, efficient platform to maximize visibility into threats. It must meet your immediate needs and scale as your organization grows. LogRhythm’s flexible foundation supports what Gartner calls “the five characteristics of an intelligence-driven SOC”:Build an Adaptive Architecture
Detect, respond to and neutralize threats on a Security Intelligence Platform purpose-built for end-to-end threat lifecycle management. Continuously evolve your environment and threatscape with LogRhythm’s extensible platform and solutions.Integrated Threat Intelligence
LogRhythm’s platform allows you to easily take advantage of a wide variety of threat intelligence sources, whether internal, commercial or open source. Our Threat Intelligence Ecosystem ensures tight integration with leading commercial sources.Leverage Advanced Analytics
Unlike traditional SIEM solutions, LogRhythm’s Security Analytics solutions analyze all data—not just a pre-filtered subset of security events. Use real-time behavioral analytics to detect threats across the holistic attack surface, including users, networks, and endpoints. Protect from the unexpected using machine learning.Hunt and Investigate
Visualize threats using interactive dashboards. Surface the most concerning attacks using risk-based prioritization. Find data quickly using precision search. Coordinate your team’s response with the industry’s leading case management function.Automate Your Responses
Formalize efficient, repeatable processes using LogRhythm’s incident response orchestration capabilities. Accelerate investigation and response activities using SmartResponse™ automation.Services to Enable Your SOC
Align Your Platform with Your Organization
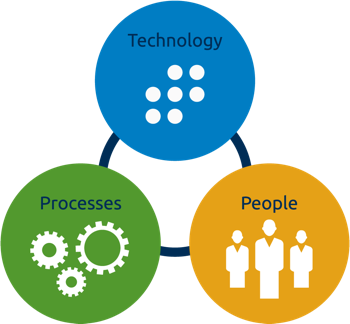
Picking the right platform is not enough—you need to align it to your business’s people, processes and technology. LogRhythm’s SOC Enablement Services help you use our Security Intelligence Platform to build the heart of your SOC: an efficient and effective monitoring and response program. With these services, we work with you to develop the three inputs most vital to the success of your SOC:
People: Maximize the value of your security team in order to build an effective and efficient monitoring and response program
Processes: Build repeatable, enabled, and automated workflows that align your Security Intelligence Platform with your organization’s functions and responsibilities
Technology: Optimally leverage environmental data and threat intelligence, detect advanced attacks with real-time machine analytics, and rapidly neutralize threats with the industry’s leading detection and response platform
Build and mature your SOC by taking advantage of our deep understanding of challenges often faced by customers, best practices for threat management, and intimate knowledge of how to use LogRhythm to optimally operationalize a SOC. Work with LogRhythm to establish clear goals for the development and implementation of your SOC and to create and execute a detailed plan to accomplish them.
Benefits of a Unified Solution
Succeeding with your SOC begins by choosing the right platform. It should address your threat management, compliance, and SIEM use cases without requiring expensive integrations or customizations. LogRhythm’s unified security operations solution reduces both your upfront and ongoing costs, lowering your total cost of ownership and maximizing your return on investment.
Advance Your Threat Management
LogRhythm’s centralized platform consolidates, normalizes, monitors, and prioritizes your security technologies and data to help you continually improve your mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR).
Meet Compliance and Regulatory Requirements
LogRhythm helps you meet stringent regulatory requirements. Streamline compliance with the purpose-built reports in our compliance automation modules. Enforce compliance in real-time with analytics rules and dashboards.
Rapidly Realize Value
LogRhythm’s unified architecture streamlines deployment and ongoing management, while out-of-the-box content helps you rapidly reach your threat management and compliance objectives.
Scale Over Time
Regardless of performance, storage or device support requirements, LogRhythm’s modular architecture gives you the flexibility and functionality you need now and as you grow.
